CMMC Starts With File Chaos
Most CMMC issues don’t start with hackers. They start when drawings and specs scatter across inboxes, desktops, and shared drives. Learn how a simple CUI lane improves control, audit readiness, and compliance.
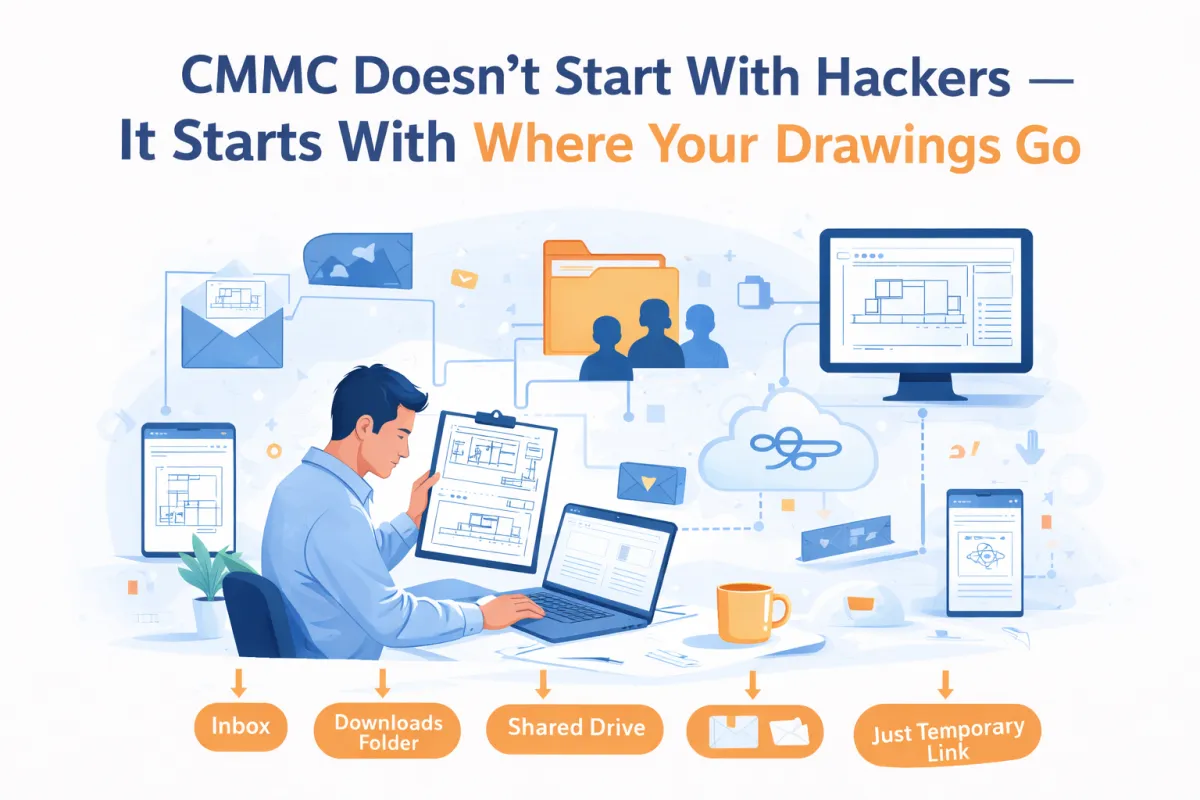
Most CMMC issues don’t start with hackers. They start when drawings and specs scatter across inboxes, desktops, and shared drives. Learn how a simple CUI lane improves control, audit readiness, and compliance.

Stronger security goes beyond “we have cameras.” This graphic highlights key protections like access control, asset security, and clearer incident tracking to help California shops stay safer and reduce risks.

A fake Zoom meeting link is being used to deliver malware that steals credentials and crypto. Learn how the scam works, what attackers target, and how to avoid malicious meeting invites.

Flat networks let ransomware spread fast across IT and OT systems. Learn how segmentation, VLAN isolation, traffic controls, and monitoring can contain threats before they shut down production.